Sha 256 hash algorithm pdf
SHA-256 and Scrypt are the two most common algorithm systems used by cryptocurrency miners in order to authenticate blocks of transaction data.
this would yield a more efficient 256 bit hashing algorithm, than the current SHA-256. We call this method SHA-512/256. We also provide a method for reducing the size of the SHA-512 constants table that an implementation will need to store. Key Words: hash algorithms, SHA-512. 1. Introduction Robust and fast security functionality is basic tenant for secure computer transactions. Hashing
SHA, which stands for secure hash algorithm, is a cryptographic hashing algorithm used to determine the integrity of a particular piece of data. Variations of this algorithm are often used by SSL certificate authorities to sign certificates. This algorithm help ensures that your website’s data is not modified or tampered with. It does so by generating
The tech world is slowly moving from SHA-1 to newer and stronger algorithms such as SHA-256. We’ve known for a few years that SHA-1 was looking weak, and now its vulnerability to attack is on full
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
2. SHA-2 Algorithm Using LabVIEW The secure hash algorithm SHA-2 steps implemented by using LabVIEW which has analyzed the LabVIEW environment capabilities for efficient implementation of cryptographic algorithms.
27/12/2016 · I’ve to create a function wherein I can calculate hash value of file using hash algorithm=”SHA-256″ encoding=”base64″ That function is to be used in Oracle 9i, 10g and 12c box (I got solution for 12c in thread Calculate hash “SHA-256” of any file (*csv,*txt,*pdf) in Oracle Directory)
SHA-256 is a cryptographic Hash function which is designed by NSA, stand for Secure Hash Algorithm, its mathematical operations which run on digital data, any person can determine the data integrity, if the one-way hash is generated from any price of data, but the data can’t be generated from the hash.
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm…
Details about the structure are published here as PDF by OASIS and here by Microsoft. Part of the definition is, that a string must be encrypted using the SHA-1 algorythm . In the first half of this article you will find examples how to encrypt a string using SHA-1 and SHA-256.
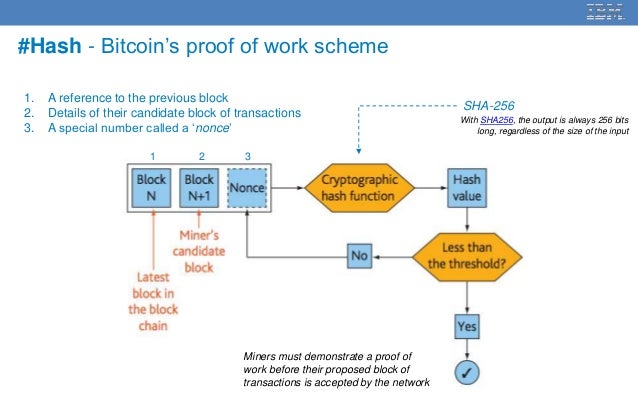
Previous Block Hash = SHA-256(SHA-256(Block Header)) The SHA-256 algorithm is also used to produce the merkle root, which is then subsequently inserted into the block header. A comprehensive explanation of this aspect of the Bitcoin protocol can be found here: Merkle Tree & …
SHA -512 algorithm and used as an input for the first compression function. Each Block is a Each Block is a 256 -bit segment of the augmented message and extended to eighty 16 -bit (64 -bit originally)
Secure Hash Algorithm (SHA) These slides are based partly on Lawrie Brown’s slides supplied withs William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 5 th Ed, 2011.
Typed again “ openssl dgst -sha256 crypto2 ” a. //hashed the file “crypto2” through message digest sha256 after bit flipped 5. Did step 2 – step 4 with message digest md5 a. //compare the hash of “crypto2” before and after bit is flipped through message digest md5 Question 4.
of their system portfolios in anticipation of the federal mandate to transition to using the SHA-256 hashing algorithm. The memo directed each organization to identify a point of contact (POC) who will provide liaison, facilitate information sharing and represent their Component to the DoD CIO. SHA-256 Support: Planning Information for Dept of Defense 4 Security at Oracle Oracle is committed
Source file. Local file: Remote URL: You can either enter a remote URL (e.g. a location where the source file is located), a local file from your device, or textual data in the field below.
SHA-256 (Secure Hash Algorithm 256) -with its message expansion modification- and MD5 (Message Digest 5) based on double-Davis-Mayer scheme to overcome the weakness existing in these functions. The proposal hash algorithm has been designed to satisfy the different levels of enhanced security and to resist the advanced hash attacks by increasing the complexity degree of the proposed hash
Introduction to the SHA-256 hash function — Steemit
https://www.youtube.com/embed/2R3dTeRBhQw
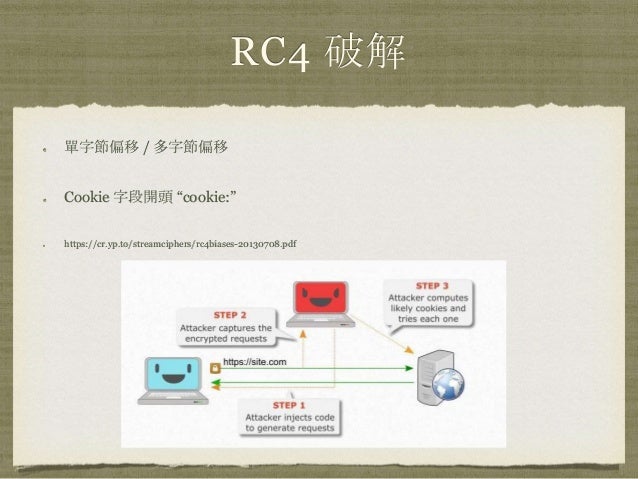
SHA-256 Planning Information for Dept of Defense
The Helion Fast Hash core family implements the NIST approved SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 secure hash algorithms to FIPS 180-3 and the legacy MD5 hash algorithm to RFC 1321. These are high performance
Introduction to the SHA-256 hash function f4tca7 ( 25 ) in cryptocurrency • last year This article aims to give an introduction into the SHA-256 hash algorithm.
SHA-256 is a message-digest algorithm. It’s used to compute a hash value in cryptography. So what’s an hash function then? Simply put, a hash function takes a block of data and returns a fixed-size bit string (hash value). The data used by hash functions is referred to as a “message”, while the computed hash value is referred to as the “message digest”.
Secure Hash Algorithm 256 or SHA 256 is defined as one of the most secure ways to protect digital information. SHA 256 is a math process that generates a 256 bit (64 character long) random sequence of letters and numbers (hash) out of any input.
Both SHA-256 and AES-256 are algorithms. Algorithm is a function, which is finite (terminates), has defined steps, ends with correct result and is generic for given problem. Both the functions satisfy these conditions, hence both are algorithms.
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA). They are built using the Merkle–Damgård structure, from a one-way compression function itself built using the Davies–Meyer structure from a …
I’ve been trying to work out how SHA-256 works. One thing I’ve been doing for other algorithms is I’ve worked out a sort of step by step pseudocode function for the algorithm.
Functional Description The Helion Fast Hash core family implements the cryptographic hash algorithms which are used wherever data integrity and/or origin authentication is a system requirement.
Unlike SHA-1, which is a 160-bit hash function, there are six SHA-2 hash functions, with a variety internal block sizes and output sizes. The most commonly used SHA-2 hash functions are SHA-256 and SHA …
The hash size for the SHA256 algorithm is 256 bits. Esta es una clase abstracta. This is an abstract class. Constructores SHA256() SHA256() SHA256() SHA256() Inicializa una nueva instancia de la clase SHA256. Initializes a new instance of SHA256. Métodos
View SHA256 algorithm profitability , hashing power, number of orders and miners on NiceHash
The SHA1 hash function is now completely unsafe Researchers have achieved the first practical SHA-1 collision, generating two PDF files with the same signature
327457-001 Overview This paper describes a family of highly-optimized implementations of the Fast SHA-256 cryptographic hash algorithm, which provide industry leading
How to compute SHA256 Hash in C#. Hashing (also known as hash functions) in cryptography is a process of mapping a binary string of an arbitrary length to a small binary string of a fixed length, known as a hash value, a hash code, or a hash.
SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm) to a known and expected hash value, a person can determine the data’s integrity. For example, computing the hash of a downloaded file and comparing the result to a previously published hash result can
bits (for SHA-384, SHA-512, SHA-512/224 and SHA-512/256) is input to a hash algorithm, the result is an output called a message digest. The message digests range in length from 160 to 512 bits, depending on the algorithm.
SHA-256 was chosen as it’s one of the most commonly used (and state-of-the-art) hash functions in existence. Also, if someone understands SHA-256, understanding the other hash functions of the SHA-2 family is an easy task.
• SHA-256 does require considerably more processor time—in our testing, there was an additional 514.5 seconds for SHA-256 to complete hashing compared to MD5, or 4.18 additional seconds per gigabyte.
SHA-256, the Secure Hash Algorithm with 256-bit digests, is not an encryption al- gorithm, but it is used in encryption protocols. The methods I discuss in this paper
PDF After recalling the basic algorithms published by NIST for implementing the hash functions SHA-256 (384, 512), a basic circuit characterized by a cascade of full adder arrays is given.
PHAL-256 (Parameterized Hash ALgorithm) is a proposal of a new dedicated hash algorithm designed as an answer to weaknesses of MD/SHA family. Recently proposed attacks on …
Basic implementations of standard cryptography algorithms, like AES and SHA-1. – B-Con/crypto-algorithms
SHA-256 (256 bit) is part of SHA-2 set of cryptographic hash functions, designed by the U.S. National Security Agency (NSA) and published in 2001 by the NIST as a U.S. Federal Information Processing Standard (FIPS). A hash function is an algorithm that transforms (hashes) an arbitrary set of data elements, such as a text file, into a single fixed length value (the hash). The computed hash
The SHA256 core is a high-performance implementation of the SHA-256 Secure Hash message digest Algorithm. This one-way hash function conforms to the 1995 US Federal Information
White Paper Fast SHA-256 Implementations Intel
The table below listed is the minimum and recommended hash size to be used with each curve. The list includes the NIST Recommended Elliptic Curves defined in FIPS PUB 186- 4: Digital Signature Standard (DSS) issued July 2013. Version Encryption algorithms PDF # Digest creation compatibility 11.0 RSA and DSA SHA1 up to 4096-bit . ECDSA (Elliptic Curve) with specific named curves (NIST
Hash Algorithms SHA-1 (Secure Hash Algorithm) NSA (1995) Successor to and replacement for MD5 Used in IPSec, SSL, TLS, PGP, SSH, and more (shows up in Java)
IS2 1 SHA-256 in FPGA Damian B. Fedoryka Abstract— SHA-256, or Secure Hash Algorithm-256, is one of the latest hash functions standardized by the U.S. Federal
SHA256 hashing algorithm which forms the basis of Bitcoin mining. These hardware optimisations have been aimed towards generic SHA256 hashing and are currently implemented and used in most mining devices. Improvements in SHA256 hardware have greatly increased the throughput and efficient implementations have also decreased the power consumption of the device. Mining typically involves
SHA-256 (Secure Hash Algorithm) is a cryptographic hash function that has certain properties which make it suitable for use in cryptography. It is a mathematical algorithm that maps data of arbitrary size to a bit string of a fixed size (a hash function) which is designed to also be a one-way function, that is, a function which is infeasible to invert .SHA – standing for secure hash algorithm – is a hash algorithm used by certification authorities to sign certificates and CRL (certificates revocation list). Introduced in 1993 by NSA with SHA0, it is used to generate unique hash values from files.
• A hash function h is (t,ε) weak collision resistant if there exists no t-time probabilistic algorithm A such that when given x, with probability > ε, it outputs x’such that x’≠x
truncated SHA-512 variants like SHA-512/256 gives a signi cant performance advantage over SHA-256 on 64-bit platforms due to the doubled input block size. At the same time, the shorter 256-bit hash values are more economic, compatible
Generate a SHA-256 hash with this free online encryption tool. To create a SHA-256 checksum of your file, use the upload feature. To further enhance the security of you encrypted hash you can use a …
Secure Hash Algorithm Message Digest Length = 256 ##### One Block Message Sample. Input Message: “abc”
Compact Implementation of KECCAK SHA3-1024 Hash Algorithm
The SHA-224 hash computations are exactly the same as those of SHA-256, up to the following two differences: The constants H 0 to H 7 used in SHA-224 are not the same as those used in SHA-256, and the SHA-224 output is obtained by truncating the final overall hash value to its 224 leftmost bits.
SHA stands for Secure Hash Algorithm. Warning SHA-256 is vulnerable to length-extension attacks , which are relevant if you are computing the hash of a secret message.
Support of 12 well-known and documented hash and checksum algorithms: MD2, MD4, MD5, SHA-1, SHA-2( 256, 384, 512), RIPEMD-160, PANAMA, TIGER, ADLER32, CRC32. Support of a custom hash algorithm ( MD4 -based) used in eDonkey and eMule applications.
Sha-256 is a one way hashing function meaning that it uses your input as a seed and returns an output of fixed length (in this case 256 bits). The algorithm is deterministic and seemingly random. This means that for any given input it will return the same output but when put up against statistical testing there is no correlation between the input and output.
In case the use of SHA1 algorithm depends on the presence of a “Seed Value” applied to an existing signature field in a PDF document (see this page), then the user can request the author of the document to update it to support SHA256 or other stronger hash algorithms, unless SHA1 is strictly necessary.
This paper attempts to infer Secure Hash Algorithm (SHA) weaknesses without actually identifying the root cause. By examining the message digest generated from a given hash function statistical patterns are examined that could indicate algorithm weaknesses. This paper presents an analysis of the SHA-256 algorithm by analyzing 2-bit distributions extracted from the message digests. The test
6/06/2016 · This video is part of the Udacity course “Intro to Information Security”. Watch the full course at https://www.udacity.com/course/ud459.
Secure Hash Algorithm-Message Digest Length = 256
Hash Sha256 Encryption and reverse decryption
https://www.youtube.com/embed/mbekM2ErHfM
10/11/2012 · but it always is signed with hash algorithm SHA-1 The hardware vendor of the smartcard, says that the problem is an adobe problem, because signing the file with its legacy software all works fine, and with its software the digest is SHA-256 (but the produced file is obviously not a signed pdf..)
TI’s SHA-256 software download help users get up and running faster, reducing time to market. Software description and features provided along with supporting documentation and resources.
found in SHA-256 and SHA-512 [44], but the common heritage and design principles of all these functions makes them suspect. More seriously, if SHA-256 and SHA-512 were to be broken, the
SHA-256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Hash is a one way function – it cannot be decrypted back. This makes it suitable for password validation, challenge hash authentication, anti-tamper, digital signatures.
The SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. This is a one-way function, so the result cannot be decrypted back to the original value.
Optimising the SHA256 Hashing Algorithm for Faster & More

SHA-256 Secure Hash Standard TI.com
SHA-256 Hashing in Java Baeldung
types of poverty in india pdf
Analysis of SHA-512/224 and SHA-512/256
SHA-256 hash calculator. Online SHA-256 hash generator
SHA256 SHA1 SHA256 (9.1) SHA1 adobe.com
SHA-256 in FPGA George Mason University

FIPS PUB 180-4 Secure Hash Standard (SHS) NIST Page
The SHA1 hash function is now completely unsafe
Hash Sha256 Encryption and reverse decryption
Atmel AVR232 Authentication Using SHA-256
SHA256 hashing algorithm which forms the basis of Bitcoin mining. These hardware optimisations have been aimed towards generic SHA256 hashing and are currently implemented and used in most mining devices. Improvements in SHA256 hardware have greatly increased the throughput and efficient implementations have also decreased the power consumption of the device. Mining typically involves
Secure Hash Algorithm (SHA) These slides are based partly on Lawrie Brown’s slides supplied withs William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 5 th Ed, 2011.
IS2 1 SHA-256 in FPGA Damian B. Fedoryka Abstract— SHA-256, or Secure Hash Algorithm-256, is one of the latest hash functions standardized by the U.S. Federal
6/06/2016 · This video is part of the Udacity course “Intro to Information Security”. Watch the full course at https://www.udacity.com/course/ud459.
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
In case the use of SHA1 algorithm depends on the presence of a “Seed Value” applied to an existing signature field in a PDF document (see this page), then the user can request the author of the document to update it to support SHA256 or other stronger hash algorithms, unless SHA1 is strictly necessary.
The SHA-224 hash computations are exactly the same as those of SHA-256, up to the following two differences: The constants H 0 to H 7 used in SHA-224 are not the same as those used in SHA-256, and the SHA-224 output is obtained by truncating the final overall hash value to its 224 leftmost bits.
SHA-256, the Secure Hash Algorithm with 256-bit digests, is not an encryption al- gorithm, but it is used in encryption protocols. The methods I discuss in this paper
Functional Description The Helion Fast Hash core family implements the cryptographic hash algorithms which are used wherever data integrity and/or origin authentication is a system requirement.
What is the Real Impact of SHA-256? A Comparison of
(PDF) The design of a high speed ASIC unit for the hash
27/12/2016 · I’ve to create a function wherein I can calculate hash value of file using hash algorithm=”SHA-256″ encoding=”base64″ That function is to be used in Oracle 9i, 10g and 12c box (I got solution for 12c in thread Calculate hash “SHA-256” of any file (*csv,*txt,*pdf) in Oracle Directory)
SHA stands for Secure Hash Algorithm. Warning SHA-256 is vulnerable to length-extension attacks , which are relevant if you are computing the hash of a secret message.
Typed again “ openssl dgst -sha256 crypto2 ” a. //hashed the file “crypto2” through message digest sha256 after bit flipped 5. Did step 2 – step 4 with message digest md5 a. //compare the hash of “crypto2” before and after bit is flipped through message digest md5 Question 4.
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
SHA-256 hash calculator Full stack and Blockchain developer
Calculate hash value using algorithm=”SHA-… Oracle
SHA-256 (Secure Hash Algorithm 256) -with its message expansion modification- and MD5 (Message Digest 5) based on double-Davis-Mayer scheme to overcome the weakness existing in these functions. The proposal hash algorithm has been designed to satisfy the different levels of enhanced security and to resist the advanced hash attacks by increasing the complexity degree of the proposed hash
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
The SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. This is a one-way function, so the result cannot be decrypted back to the original value.
Basic implementations of standard cryptography algorithms, like AES and SHA-1. – B-Con/crypto-algorithms
PDF After recalling the basic algorithms published by NIST for implementing the hash functions SHA-256 (384, 512), a basic circuit characterized by a cascade of full adder arrays is given.
SHA-256 (256 bit) is part of SHA-2 set of cryptographic hash functions, designed by the U.S. National Security Agency (NSA) and published in 2001 by the NIST as a U.S. Federal Information Processing Standard (FIPS). A hash function is an algorithm that transforms (hashes) an arbitrary set of data elements, such as a text file, into a single fixed length value (the hash). The computed hash
Previous Block Hash = SHA-256(SHA-256(Block Header)) The SHA-256 algorithm is also used to produce the merkle root, which is then subsequently inserted into the block header. A comprehensive explanation of this aspect of the Bitcoin protocol can be found here: Merkle Tree & …
All about SHA1 SHA2 and SHA256 hash algorithms
SHA1 vs SHA256 KeyCDN Support
The table below listed is the minimum and recommended hash size to be used with each curve. The list includes the NIST Recommended Elliptic Curves defined in FIPS PUB 186- 4: Digital Signature Standard (DSS) issued July 2013. Version Encryption algorithms PDF # Digest creation compatibility 11.0 RSA and DSA SHA1 up to 4096-bit . ECDSA (Elliptic Curve) with specific named curves (NIST
• A hash function h is (t,ε) weak collision resistant if there exists no t-time probabilistic algorithm A such that when given x, with probability > ε, it outputs x’such that x’≠x
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm…
Unlike SHA-1, which is a 160-bit hash function, there are six SHA-2 hash functions, with a variety internal block sizes and output sizes. The most commonly used SHA-2 hash functions are SHA-256 and SHA …
Applying a digital signature using the deprecated SHA1
SHA-1 Versus SHA-2 Overview CA Security Council
• A hash function h is (t,ε) weak collision resistant if there exists no t-time probabilistic algorithm A such that when given x, with probability > ε, it outputs x’such that x’≠x
The SHA-224 hash computations are exactly the same as those of SHA-256, up to the following two differences: The constants H 0 to H 7 used in SHA-224 are not the same as those used in SHA-256, and the SHA-224 output is obtained by truncating the final overall hash value to its 224 leftmost bits.
6/06/2016 · This video is part of the Udacity course “Intro to Information Security”. Watch the full course at https://www.udacity.com/course/ud459.
10/11/2012 · but it always is signed with hash algorithm SHA-1 The hardware vendor of the smartcard, says that the problem is an adobe problem, because signing the file with its legacy software all works fine, and with its software the digest is SHA-256 (but the produced file is obviously not a signed pdf..)
• SHA-256 does require considerably more processor time—in our testing, there was an additional 514.5 seconds for SHA-256 to complete hashing compared to MD5, or 4.18 additional seconds per gigabyte.
Unlike SHA-1, which is a 160-bit hash function, there are six SHA-2 hash functions, with a variety internal block sizes and output sizes. The most commonly used SHA-2 hash functions are SHA-256 and SHA …
The table below listed is the minimum and recommended hash size to be used with each curve. The list includes the NIST Recommended Elliptic Curves defined in FIPS PUB 186- 4: Digital Signature Standard (DSS) issued July 2013. Version Encryption algorithms PDF # Digest creation compatibility 11.0 RSA and DSA SHA1 up to 4096-bit . ECDSA (Elliptic Curve) with specific named curves (NIST
How to compute SHA256 Hash in C#. Hashing (also known as hash functions) in cryptography is a process of mapping a binary string of an arbitrary length to a small binary string of a fixed length, known as a hash value, a hash code, or a hash.
Introduction to the SHA-256 hash function f4tca7 ( 25 ) in cryptocurrency • last year This article aims to give an introduction into the SHA-256 hash algorithm.
SHA-256 and Scrypt are the two most common algorithm systems used by cryptocurrency miners in order to authenticate blocks of transaction data.
of their system portfolios in anticipation of the federal mandate to transition to using the SHA-256 hashing algorithm. The memo directed each organization to identify a point of contact (POC) who will provide liaison, facilitate information sharing and represent their Component to the DoD CIO. SHA-256 Support: Planning Information for Dept of Defense 4 Security at Oracle Oracle is committed
2. SHA-2 Algorithm Using LabVIEW The secure hash algorithm SHA-2 steps implemented by using LabVIEW which has analyzed the LabVIEW environment capabilities for efficient implementation of cryptographic algorithms.
Atmel AVR232 Authentication Using SHA-256
Verification of a Cryptographic Primitive SHA-256
Both SHA-256 and AES-256 are algorithms. Algorithm is a function, which is finite (terminates), has defined steps, ends with correct result and is generic for given problem. Both the functions satisfy these conditions, hence both are algorithms.
The Helion Fast Hash core family implements the NIST approved SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 secure hash algorithms to FIPS 180-3 and the legacy MD5 hash algorithm to RFC 1321. These are high performance
2. SHA-2 Algorithm Using LabVIEW The secure hash algorithm SHA-2 steps implemented by using LabVIEW which has analyzed the LabVIEW environment capabilities for efficient implementation of cryptographic algorithms.
PHAL-256 (Parameterized Hash ALgorithm) is a proposal of a new dedicated hash algorithm designed as an answer to weaknesses of MD/SHA family. Recently proposed attacks on …
White Paper Fast SHA-256 Implementations Intel
(PDF) The design of a high speed ASIC unit for the hash
SHA-256 is a message-digest algorithm. It’s used to compute a hash value in cryptography. So what’s an hash function then? Simply put, a hash function takes a block of data and returns a fixed-size bit string (hash value). The data used by hash functions is referred to as a “message”, while the computed hash value is referred to as the “message digest”.
This paper attempts to infer Secure Hash Algorithm (SHA) weaknesses without actually identifying the root cause. By examining the message digest generated from a given hash function statistical patterns are examined that could indicate algorithm weaknesses. This paper presents an analysis of the SHA-256 algorithm by analyzing 2-bit distributions extracted from the message digests. The test
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm…
Basic implementations of standard cryptography algorithms, like AES and SHA-1. – B-Con/crypto-algorithms
SHA-256 (Secure Hash Algorithm 256) -with its message expansion modification- and MD5 (Message Digest 5) based on double-Davis-Mayer scheme to overcome the weakness existing in these functions. The proposal hash algorithm has been designed to satisfy the different levels of enhanced security and to resist the advanced hash attacks by increasing the complexity degree of the proposed hash
SHA256 hashing algorithm which forms the basis of Bitcoin mining. These hardware optimisations have been aimed towards generic SHA256 hashing and are currently implemented and used in most mining devices. Improvements in SHA256 hardware have greatly increased the throughput and efficient implementations have also decreased the power consumption of the device. Mining typically involves
SHA, which stands for secure hash algorithm, is a cryptographic hashing algorithm used to determine the integrity of a particular piece of data. Variations of this algorithm are often used by SSL certificate authorities to sign certificates. This algorithm help ensures that your website’s data is not modified or tampered with. It does so by generating
How to compute SHA256 Hash in C#. Hashing (also known as hash functions) in cryptography is a process of mapping a binary string of an arbitrary length to a small binary string of a fixed length, known as a hash value, a hash code, or a hash.
Secure Hash Algorithm Message Digest Length = 256 ##### One Block Message Sample. Input Message: “abc”
• A hash function h is (t,ε) weak collision resistant if there exists no t-time probabilistic algorithm A such that when given x, with probability > ε, it outputs x’such that x’≠x
• SHA-256 does require considerably more processor time—in our testing, there was an additional 514.5 seconds for SHA-256 to complete hashing compared to MD5, or 4.18 additional seconds per gigabyte.
SHA-256 in FPGA George Mason University
SHA256 Class (System.Security.Cryptography) Microsoft Docs
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA). They are built using the Merkle–Damgård structure, from a one-way compression function itself built using the Davies–Meyer structure from a …
The Helion Fast Hash core family implements the NIST approved SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 secure hash algorithms to FIPS 180-3 and the legacy MD5 hash algorithm to RFC 1321. These are high performance
Functional Description The Helion Fast Hash core family implements the cryptographic hash algorithms which are used wherever data integrity and/or origin authentication is a system requirement.
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
• SHA-256 does require considerably more processor time—in our testing, there was an additional 514.5 seconds for SHA-256 to complete hashing compared to MD5, or 4.18 additional seconds per gigabyte.
SHA-256 (Secure Hash Algorithm) is a cryptographic hash function that has certain properties which make it suitable for use in cryptography. It is a mathematical algorithm that maps data of arbitrary size to a bit string of a fixed size (a hash function) which is designed to also be a one-way function, that is, a function which is infeasible to invert .
FIPS PUB 180-4 Secure Hash Standard (SHS) NIST Page
What is SHA-256 (The cryptography hash function)
• SHA-256 does require considerably more processor time—in our testing, there was an additional 514.5 seconds for SHA-256 to complete hashing compared to MD5, or 4.18 additional seconds per gigabyte.
SHA-256 (Secure Hash Algorithm 256) -with its message expansion modification- and MD5 (Message Digest 5) based on double-Davis-Mayer scheme to overcome the weakness existing in these functions. The proposal hash algorithm has been designed to satisfy the different levels of enhanced security and to resist the advanced hash attacks by increasing the complexity degree of the proposed hash
Basic implementations of standard cryptography algorithms, like AES and SHA-1. – B-Con/crypto-algorithms
Sha-256 is a one way hashing function meaning that it uses your input as a seed and returns an output of fixed length (in this case 256 bits). The algorithm is deterministic and seemingly random. This means that for any given input it will return the same output but when put up against statistical testing there is no correlation between the input and output.
SHA-256 is a message-digest algorithm. It’s used to compute a hash value in cryptography. So what’s an hash function then? Simply put, a hash function takes a block of data and returns a fixed-size bit string (hash value). The data used by hash functions is referred to as a “message”, while the computed hash value is referred to as the “message digest”.
327457-001 Overview This paper describes a family of highly-optimized implementations of the Fast SHA-256 cryptographic hash algorithm, which provide industry leading
The hash size for the SHA256 algorithm is 256 bits. Esta es una clase abstracta. This is an abstract class. Constructores SHA256() SHA256() SHA256() SHA256() Inicializa una nueva instancia de la clase SHA256. Initializes a new instance of SHA256. Métodos
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm…
6/06/2016 · This video is part of the Udacity course “Intro to Information Security”. Watch the full course at https://www.udacity.com/course/ud459.
SHA-0 SHA-1 SHA-2 (Secure Hash Algorithm) SpringerLink
Calculate hash value using algorithm=”SHA-… Oracle
Source file. Local file: Remote URL: You can either enter a remote URL (e.g. a location where the source file is located), a local file from your device, or textual data in the field below.
SHA-256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Hash is a one way function – it cannot be decrypted back. This makes it suitable for password validation, challenge hash authentication, anti-tamper, digital signatures.
PHAL-256 (Parameterized Hash ALgorithm) is a proposal of a new dedicated hash algorithm designed as an answer to weaknesses of MD/SHA family. Recently proposed attacks on …
The Helion Fast Hash core family implements the NIST approved SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 secure hash algorithms to FIPS 180-3 and the legacy MD5 hash algorithm to RFC 1321. These are high performance
How to compute SHA256 Hash in C#. Hashing (also known as hash functions) in cryptography is a process of mapping a binary string of an arbitrary length to a small binary string of a fixed length, known as a hash value, a hash code, or a hash.
I’ve been trying to work out how SHA-256 works. One thing I’ve been doing for other algorithms is I’ve worked out a sort of step by step pseudocode function for the algorithm.
View SHA256 algorithm profitability , hashing power, number of orders and miners on NiceHash
PDF After recalling the basic algorithms published by NIST for implementing the hash functions SHA-256 (384, 512), a basic circuit characterized by a cascade of full adder arrays is given.
Functional Description The Helion Fast Hash core family implements the cryptographic hash algorithms which are used wherever data integrity and/or origin authentication is a system requirement.
Both SHA-256 and AES-256 are algorithms. Algorithm is a function, which is finite (terminates), has defined steps, ends with correct result and is generic for given problem. Both the functions satisfy these conditions, hence both are algorithms.
Typed again “ openssl dgst -sha256 crypto2 ” a. //hashed the file “crypto2” through message digest sha256 after bit flipped 5. Did step 2 – step 4 with message digest md5 a. //compare the hash of “crypto2” before and after bit is flipped through message digest md5 Question 4.
SHA-256 was chosen as it’s one of the most commonly used (and state-of-the-art) hash functions in existence. Also, if someone understands SHA-256, understanding the other hash functions of the SHA-2 family is an easy task.
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
SHA-256 Generator freeformatter
What is SHA-256 (The cryptography hash function)
SHA-256 and Scrypt are the two most common algorithm systems used by cryptocurrency miners in order to authenticate blocks of transaction data.
How to compute SHA256 Hash in C#. Hashing (also known as hash functions) in cryptography is a process of mapping a binary string of an arbitrary length to a small binary string of a fixed length, known as a hash value, a hash code, or a hash.
of their system portfolios in anticipation of the federal mandate to transition to using the SHA-256 hashing algorithm. The memo directed each organization to identify a point of contact (POC) who will provide liaison, facilitate information sharing and represent their Component to the DoD CIO. SHA-256 Support: Planning Information for Dept of Defense 4 Security at Oracle Oracle is committed
Source file. Local file: Remote URL: You can either enter a remote URL (e.g. a location where the source file is located), a local file from your device, or textual data in the field below.
javascript SHA-256 algorithm and/or de-hashing algorithm
Secure Hash Algorithm-Message Digest Length = 256
Basic implementations of standard cryptography algorithms, like AES and SHA-1. – B-Con/crypto-algorithms
found in SHA-256 and SHA-512 [44], but the common heritage and design principles of all these functions makes them suspect. More seriously, if SHA-256 and SHA-512 were to be broken, the
SHA256 hashing algorithm which forms the basis of Bitcoin mining. These hardware optimisations have been aimed towards generic SHA256 hashing and are currently implemented and used in most mining devices. Improvements in SHA256 hardware have greatly increased the throughput and efficient implementations have also decreased the power consumption of the device. Mining typically involves
SHA -512 algorithm and used as an input for the first compression function. Each Block is a Each Block is a 256 -bit segment of the augmented message and extended to eighty 16 -bit (64 -bit originally)
SHA-0 SHA-1 SHA-2 (Secure Hash Algorithm) SpringerLink
Compute SHA256 Hash In C# c-sharpcorner.com
Sha-256 is a one way hashing function meaning that it uses your input as a seed and returns an output of fixed length (in this case 256 bits). The algorithm is deterministic and seemingly random. This means that for any given input it will return the same output but when put up against statistical testing there is no correlation between the input and output.
SHA -512 algorithm and used as an input for the first compression function. Each Block is a Each Block is a 256 -bit segment of the augmented message and extended to eighty 16 -bit (64 -bit originally)
Secure Hash Algorithm (SHA) These slides are based partly on Lawrie Brown’s slides supplied withs William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 5 th Ed, 2011.
Source file. Local file: Remote URL: You can either enter a remote URL (e.g. a location where the source file is located), a local file from your device, or textual data in the field below.
The table below listed is the minimum and recommended hash size to be used with each curve. The list includes the NIST Recommended Elliptic Curves defined in FIPS PUB 186- 4: Digital Signature Standard (DSS) issued July 2013. Version Encryption algorithms PDF # Digest creation compatibility 11.0 RSA and DSA SHA1 up to 4096-bit . ECDSA (Elliptic Curve) with specific named curves (NIST
bits (for SHA-384, SHA-512, SHA-512/224 and SHA-512/256) is input to a hash algorithm, the result is an output called a message digest. The message digests range in length from 160 to 512 bits, depending on the algorithm.
TI’s SHA-256 software download help users get up and running faster, reducing time to market. Software description and features provided along with supporting documentation and resources.
The hash size for the SHA256 algorithm is 256 bits. Esta es una clase abstracta. This is an abstract class. Constructores SHA256() SHA256() SHA256() SHA256() Inicializa una nueva instancia de la clase SHA256. Initializes a new instance of SHA256. Métodos
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
SHA-256 (Secure Hash Algorithm 256) -with its message expansion modification- and MD5 (Message Digest 5) based on double-Davis-Mayer scheme to overcome the weakness existing in these functions. The proposal hash algorithm has been designed to satisfy the different levels of enhanced security and to resist the advanced hash attacks by increasing the complexity degree of the proposed hash
Calculate hash value using algorithm=”SHA-… Oracle
Hash Algorithms University of Cincinnati
The SHA-224 hash computations are exactly the same as those of SHA-256, up to the following two differences: The constants H 0 to H 7 used in SHA-224 are not the same as those used in SHA-256, and the SHA-224 output is obtained by truncating the final overall hash value to its 224 leftmost bits.
Introduction to the SHA-256 hash function f4tca7 ( 25 ) in cryptocurrency • last year This article aims to give an introduction into the SHA-256 hash algorithm.
Source file. Local file: Remote URL: You can either enter a remote URL (e.g. a location where the source file is located), a local file from your device, or textual data in the field below.
found in SHA-256 and SHA-512 [44], but the common heritage and design principles of all these functions makes them suspect. More seriously, if SHA-256 and SHA-512 were to be broken, the
SHA-256 — PyCryptodome 3.7.2 documentation
Introduction to The SHA-256 Hash Function – Laikelib
Typed again “ openssl dgst -sha256 crypto2 ” a. //hashed the file “crypto2” through message digest sha256 after bit flipped 5. Did step 2 – step 4 with message digest md5 a. //compare the hash of “crypto2” before and after bit is flipped through message digest md5 Question 4.
SHA -512 algorithm and used as an input for the first compression function. Each Block is a Each Block is a 256 -bit segment of the augmented message and extended to eighty 16 -bit (64 -bit originally)
Functional Description The Helion Fast Hash core family implements the cryptographic hash algorithms which are used wherever data integrity and/or origin authentication is a system requirement.
PDF After recalling the basic algorithms published by NIST for implementing the hash functions SHA-256 (384, 512), a basic circuit characterized by a cascade of full adder arrays is given.
SHA, which stands for secure hash algorithm, is a cryptographic hashing algorithm used to determine the integrity of a particular piece of data. Variations of this algorithm are often used by SSL certificate authorities to sign certificates. This algorithm help ensures that your website’s data is not modified or tampered with. It does so by generating
SHA-256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Hash is a one way function – it cannot be decrypted back. This makes it suitable for password validation, challenge hash authentication, anti-tamper, digital signatures.
Details about the structure are published here as PDF by OASIS and here by Microsoft. Part of the definition is, that a string must be encrypted using the SHA-1 algorythm . In the first half of this article you will find examples how to encrypt a string using SHA-1 and SHA-256.
27/12/2016 · I’ve to create a function wherein I can calculate hash value of file using hash algorithm=”SHA-256″ encoding=”base64″ That function is to be used in Oracle 9i, 10g and 12c box (I got solution for 12c in thread Calculate hash “SHA-256” of any file (*csv,*txt,*pdf) in Oracle Directory)
bits (for SHA-384, SHA-512, SHA-512/224 and SHA-512/256) is input to a hash algorithm, the result is an output called a message digest. The message digests range in length from 160 to 512 bits, depending on the algorithm.
SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm) to a known and expected hash value, a person can determine the data’s integrity. For example, computing the hash of a downloaded file and comparing the result to a previously published hash result can
Secure Hash Algorithm (SHA) These slides are based partly on Lawrie Brown’s slides supplied withs William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 5 th Ed, 2011.
Both SHA-256 and AES-256 are algorithms. Algorithm is a function, which is finite (terminates), has defined steps, ends with correct result and is generic for given problem. Both the functions satisfy these conditions, hence both are algorithms.
Calculate hash value using algorithm=”SHA-… Oracle
SHA-256 in FPGA George Mason University
Atmel AVR232: Authentication Using SHA-256 [APPLICATION NOTE] 8184A−AVR−09/2012 3 There is no difference in security between using an encryption or keyed-hash, other than the …
Typed again “ openssl dgst -sha256 crypto2 ” a. //hashed the file “crypto2” through message digest sha256 after bit flipped 5. Did step 2 – step 4 with message digest md5 a. //compare the hash of “crypto2” before and after bit is flipped through message digest md5 Question 4.
SHA-256 and Scrypt are the two most common algorithm systems used by cryptocurrency miners in order to authenticate blocks of transaction data.
The hash size for the SHA256 algorithm is 256 bits. Esta es una clase abstracta. This is an abstract class. Constructores SHA256() SHA256() SHA256() SHA256() Inicializa una nueva instancia de la clase SHA256. Initializes a new instance of SHA256. Métodos
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed “hash” (the output from execution of the algorithm…
Sha-256 is a one way hashing function meaning that it uses your input as a seed and returns an output of fixed length (in this case 256 bits). The algorithm is deterministic and seemingly random. This means that for any given input it will return the same output but when put up against statistical testing there is no correlation between the input and output.
The SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. This is a one-way function, so the result cannot be decrypted back to the original value.
In case the use of SHA1 algorithm depends on the presence of a “Seed Value” applied to an existing signature field in a PDF document (see this page), then the user can request the author of the document to update it to support SHA256 or other stronger hash algorithms, unless SHA1 is strictly necessary.
The table below listed is the minimum and recommended hash size to be used with each curve. The list includes the NIST Recommended Elliptic Curves defined in FIPS PUB 186- 4: Digital Signature Standard (DSS) issued July 2013. Version Encryption algorithms PDF # Digest creation compatibility 11.0 RSA and DSA SHA1 up to 4096-bit . ECDSA (Elliptic Curve) with specific named curves (NIST
SHA-256 (256 bit) is part of SHA-2 set of cryptographic hash functions, designed by the U.S. National Security Agency (NSA) and published in 2001 by the NIST as a U.S. Federal Information Processing Standard (FIPS). A hash function is an algorithm that transforms (hashes) an arbitrary set of data elements, such as a text file, into a single fixed length value (the hash). The computed hash
SHA-256 was chosen as it’s one of the most commonly used (and state-of-the-art) hash functions in existence. Also, if someone understands SHA-256, understanding the other hash functions of the SHA-2 family is an easy task.
Details about the structure are published here as PDF by OASIS and here by Microsoft. Part of the definition is, that a string must be encrypted using the SHA-1 algorythm . In the first half of this article you will find examples how to encrypt a string using SHA-1 and SHA-256.
javascript SHA-256 algorithm and/or de-hashing algorithm
Calculate hash value using algorithm=”SHA-… Oracle
PDF After recalling the basic algorithms published by NIST for implementing the hash functions SHA-256 (384, 512), a basic circuit characterized by a cascade of full adder arrays is given.
The hash size for the SHA256 algorithm is 256 bits. Esta es una clase abstracta. This is an abstract class. Constructores SHA256() SHA256() SHA256() SHA256() Inicializa una nueva instancia de la clase SHA256. Initializes a new instance of SHA256. Métodos
The Helion Fast Hash core family implements the NIST approved SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512 secure hash algorithms to FIPS 180-3 and the legacy MD5 hash algorithm to RFC 1321. These are high performance
Generate a SHA-256 hash with this free online encryption tool. To create a SHA-256 checksum of your file, use the upload feature. To further enhance the security of you encrypted hash you can use a …
Introduction to the SHA-256 hash function f4tca7 ( 25 ) in cryptocurrency • last year This article aims to give an introduction into the SHA-256 hash algorithm.
SHA-256, the Secure Hash Algorithm with 256-bit digests, is not an encryption al- gorithm, but it is used in encryption protocols. The methods I discuss in this paper
Cryptographic Hash Functions University of Texas at Dallas
SHA, which stands for secure hash algorithm, is a cryptographic hashing algorithm used to determine the integrity of a particular piece of data. Variations of this algorithm are often used by SSL certificate authorities to sign certificates. This algorithm help ensures that your website’s data is not modified or tampered with. It does so by generating
Cryptographic Hash Functions University of Texas at Dallas
SHA-256 Planning Information for Dept of Defense
Cryptographic Hash Functions cse.wustl.edu
Introduction to the SHA-256 hash function f4tca7 ( 25 ) in cryptocurrency • last year This article aims to give an introduction into the SHA-256 hash algorithm.
SHA1 vs SHA256 KeyCDN Support
SHA-256 Secure Hash Standard TI.com
The SHA-224 hash computations are exactly the same as those of SHA-256, up to the following two differences: The constants H 0 to H 7 used in SHA-224 are not the same as those used in SHA-256, and the SHA-224 output is obtained by truncating the final overall hash value to its 224 leftmost bits.
SHA-256 hash calculator Full stack and Blockchain developer
Both SHA-256 and AES-256 are algorithms. Algorithm is a function, which is finite (terminates), has defined steps, ends with correct result and is generic for given problem. Both the functions satisfy these conditions, hence both are algorithms.
Compute SHA256 Hash In C# c-sharpcorner.com
Support of 12 well-known and documented hash and checksum algorithms: MD2, MD4, MD5, SHA-1, SHA-2( 256, 384, 512), RIPEMD-160, PANAMA, TIGER, ADLER32, CRC32. Support of a custom hash algorithm ( MD4 -based) used in eDonkey and eMule applications.
(PDF) The design of a high speed ASIC unit for the hash
Hash hash baby Secure Hash Algorithm in NAV/365BC (and